news
HACKS OF TODAY 14/12/2023

Today’s HOT includes 30 victims:
17 ransomware by the notorious LockBit 3.0, RansomHouse, ALPHV/BlackCat, Knight, BlackBasta, Cloak and Meow gangs and 13 data breach by DragonForce.
The average Cyber Risk Factor is 3.8.
Read below the full list.
Disclaimer:
Data are collected from public info published on Dark Web.
The Cyber Risk factor is calculated on cyber attacks’ impact based on available data.
It shows the severity of an event: 1 = low, 5 = critical
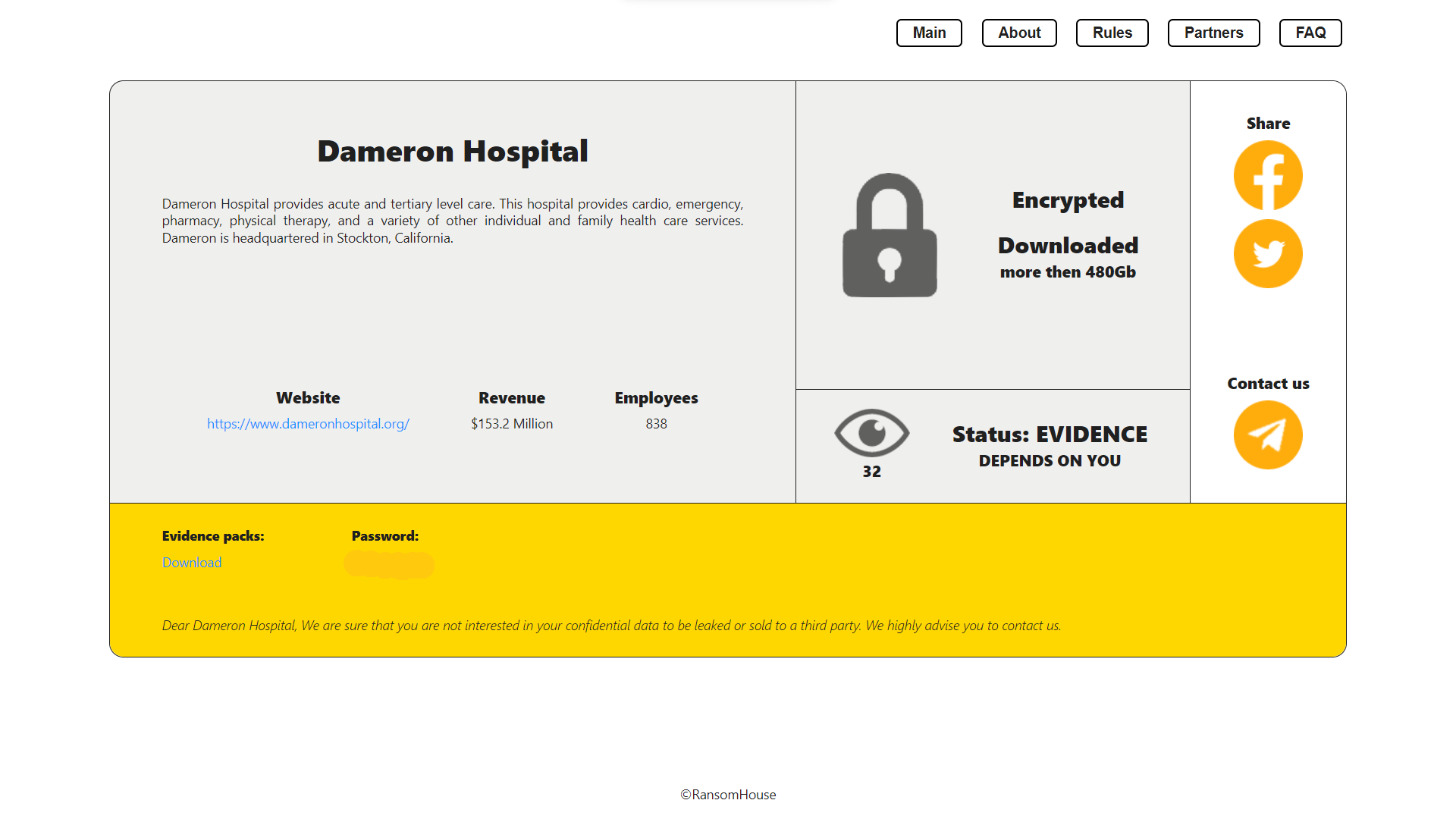
DAMERON HOSPITAL
Victim website: | dameronhospital.org |
Victim country: | USA |
Attacker name: | RansomHouse |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 480 GB |
Exfiltrated data type: | N/A |
Leaked data: | Sample |
Ransom deadline: | N/A |
Cyber Risk Factor: | 5 |
Image: |
ADVANTAGE GROUP INTERNATIONAL
Victim website: | advantagegroup.com |
Victim country: | Canada |
Attacker name: | ALPHV/BlackCat |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 8 TB |
Exfiltrated data type: | Massive datasets from clients such as Coca Cola, Procter & Gamble, and Pepsi. The data breach includes a significant amount of personally identifiable information (PII) such as social security numbers and driver’s license numbers, non-disclosure agreements, legal cases, and other sensitive documents, passwords, etc. |
Leaked data: | Sample |
Ransom deadline: | N/A |
Cyber Risk Factor: | 5 |
Image: |
CITY OF DEFIANCE
Victim website: | cityofdefiance.com |
Victim country: | USA |
Attacker name: | Knight |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 390 GB |
Exfiltrated data type: | Employees’ file, law enforcement video, confidential documents, etc. |
Leaked data: | Sample |
Ransom deadline: | 23rd Dec 23 |
Cyber Risk Factor: | 5 |
Image: |
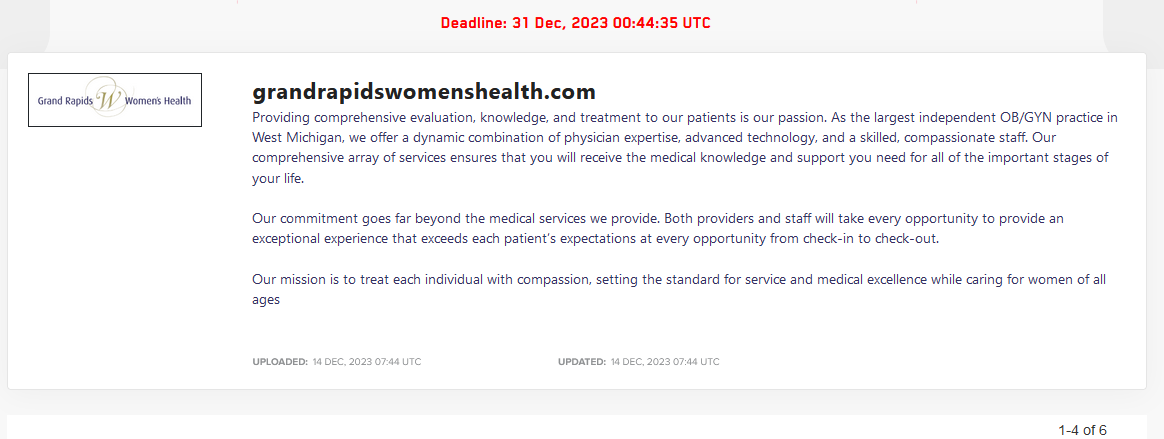
GRAND RAPIDS WOMEN’S HEALTH
Victim website: | grandrapidswomenshealth.com |
Victim country: | USA |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 453 GB |
Exfiltrated data type: | Reports, scans, invoices, forms, etc. |
Leaked data: | Sample |
Ransom deadline: | 31st Dec 23 |
Cyber Risk Factor: | 5 |
Image: |
CAROLINA BEVERAGE GROUP
Victim website: | carolinabeveragegroup.com |
Victim country: | USA |
Attacker name: | BlackBasta |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 316 GB |
Exfiltrated data type: | Accounting records, I-9 forms, 401K forms, and more |
Leaked data: | Sample |
Ransom deadline: | 21st Dec 23 |
Cyber Risk Factor: | 4 |
Image: |
THIRD STREET BREWHOUSE
Victim website: | thirdstreetbrewhouse.com |
Victim country: | USA |
Attacker name: | BlackBasta |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 316 GB |
Exfiltrated data type: | Accounting records, I-9 forms, 401K forms, and more |
Leaked data: | Sample |
Ransom deadline: | 21st Dec 23 |
Cyber Risk Factor: | 4 |
Image: |
TULANE UNIVERSITY
Victim website: | tulane.edu |
Victim country: | USA |
Attacker name: | Meow |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | N/A |
Cyber Risk Factor: | 3 |
Image: |
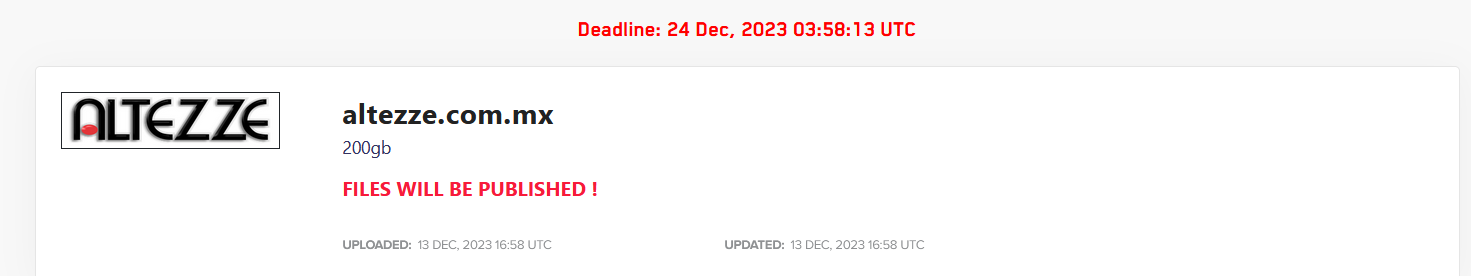
ALTEZZE
Victim website: | altezze.com.mx |
Victim country: | Mexico |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 200 GB |
Exfiltrated data type: | Miscellaneous including ID cards |
Leaked data: | Sample |
Ransom deadline: | 24th Dec 23 |
Cyber Risk Factor: | 4 |
Image: |
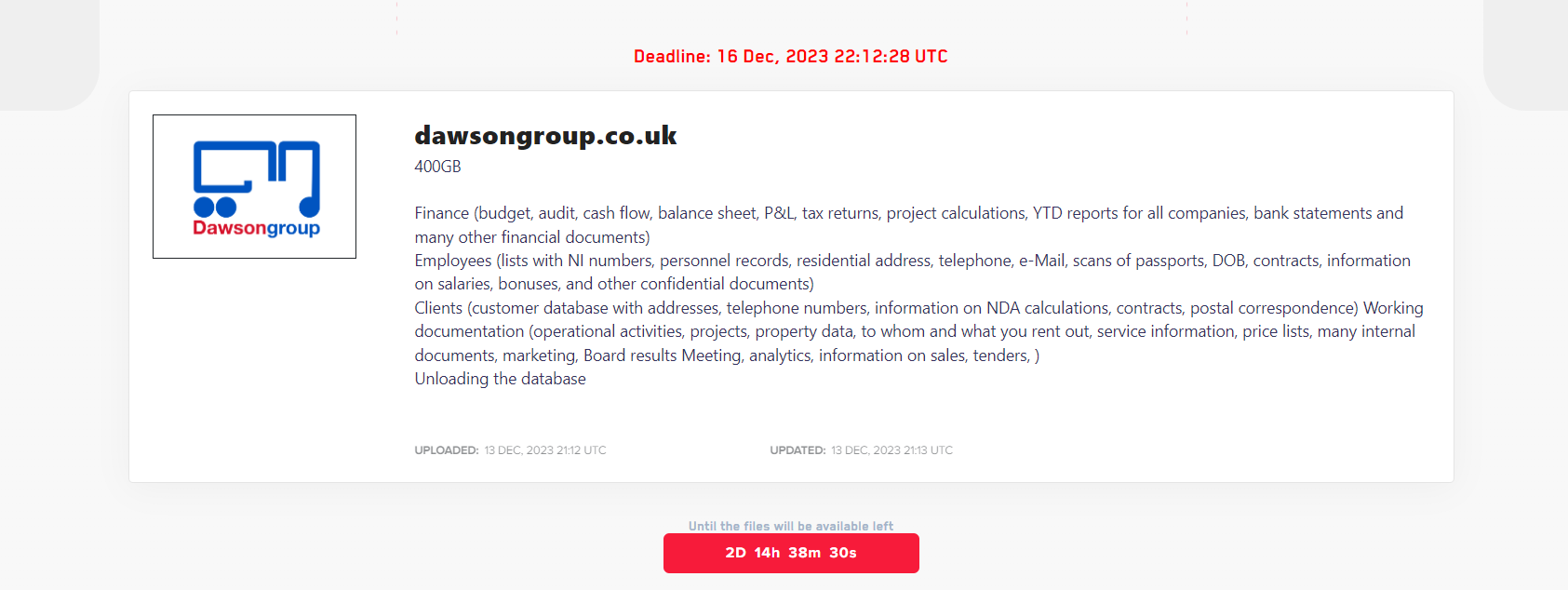
DAWSONGROUP
Victim website: | dawsongroup.co.uk |
Victim country: | United Kingdom |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 400 GB |
Exfiltrated data type: | Information related to finance, employees, clients, and more |
Leaked data: | / |
Ransom deadline: | 16th Dec 23 |
Cyber Risk Factor: | 4 |
Image: |
CATHOLIC CHARITIES OF THE ARCHDIOCESE MIAMI
Victim website: | ccadm.org |
Victim country: | USA |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | ID cards, confidential documents, employees’ data, etc. |
Leaked data: | Sample |
Ransom deadline: | 02nd Jan 24 |
Cyber Risk Factor: | 4 |
Image: |
GAIDO & FINTZEN
Victim website: | Gaido-fintzen.com |
Victim country: | USA |
Attacker name: | Cloak |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | 18th Dec 23 |
Cyber Risk Factor: | 3 |
Image: |
AKIR METAL SAN TIC
Victim website: | akimmetal.com.tr |
Victim country: | Turkey |
Attacker name: | Knight |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | NDA documents, personal data, insurance data, financial documents, engineering information, patents, technological developments and R&D documents, confidential customer information, employee and management correspondence and internal data, and other critical documents of the company and its customers. |
Leaked data: | / |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: | Not available |
AUSTEN CONSULTANTS
Victim website: | austen-it.com |
Victim country: | USA |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | 20th Dec 23 |
Cyber Risk Factor: | 4 |
Image: |
HEART OF TEXAS BEHAVIORAL HEALTH NETWORK (added to the DLS on 06/12/23)
Victim website: | hotrmhmr.org |
Victim country: | USA |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 55.78 GB |
Exfiltrated data type: | Personal data, ID, passports, and company documents. |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
PCTEL (added to the DLS on 06/12/23)
Victim website: | pctel.com |
Victim country: | USA |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 267.56 GB |
Exfiltrated data type: | Financial documents, passports, etc. |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
AGL WELDING SUPPLY
Victim website: | aglgases.com |
Victim country: | USA |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 171,54 GB |
Exfiltrated data type: | N/A |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
GRAYHILL
Victim website: | grayhill.com |
Victim country: | USA |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 19.71 |
Exfiltrated data type: | Confidential documents |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
LEEDARSON LIGHTING
Victim website: | leedarson.com |
Victim country: | China |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 3.53 GB |
Exfiltrated data type: | Confidential documents |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 3 |
Image: |
COCA-COLA SINGAPORE
Victim website: | coca-cola.com.sg |
Victim country: | Singapore |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 413.92 GB |
Exfiltrated data type: | Backup reports, Customer information, etc. |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
SHORTS
Victim website: | shorts.uk.com |
Victim country: | United Kingdom |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 597.67 GB |
Exfiltrated data type: | TAX reports, Pension, Income, Salaries, Scans etc. |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
WORLD EMBLEM INTERNATIONAL
Victim website: | worldemblem.com |
Victim country: | USA |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 417.12 GB |
Exfiltrated data type: | Miscellaneous documents, Orders, insurance, design, employee details, etc. |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
CINQCARE
Victim website: | gbuahn.org |
Victim country: | USA |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 235.66 GB |
Exfiltrated data type: | Finances, Backups, Employees’ health documents etc. |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
STADT BADEN
Victim website: | baden.ch |
Victim country: | Switzerland |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 3 GB |
Exfiltrated data type: | City database |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 3 |
Image: |
DAFITI ARGENTINA
Victim website: | dafiti.com.ar |
Victim country: | Argentina |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 321.63 GB |
Exfiltrated data type: | N/A |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
LUNACON CONSTRUCTION GROUP
Victim website: | lunaconcorp.com |
Victim country: | USA |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 50.93 GB |
Exfiltrated data type: | Contracts, Personal data etc. |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
TGLT
Victim website: | tglt.com |
Victim country: | Argentina |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 158.78 GB |
Exfiltrated data type: | N/A |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 3 |
Image: |
SEVEN SEAS GROUP
Victim website: | sevenseasgroup.com |
Victim country: | UAE |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 26.52 GB |
Exfiltrated data type: | N/A |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
DECINA BATHROOMWARE
Victim website: | decina.com.au |
Victim country: | Australia |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 108.98 GB |
Exfiltrated data type: | N/A |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 3 |
Image: |
COOPER RESEARCH TECHNOLOGY
Victim website: | cooper.co.uk |
Victim country: | United Kingdom |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 64.72 GB |
Exfiltrated data type: | Financial documents |
Leaked data: | 100% of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
GREATER CINCINNATI BEHAVIORAL HEALTH SERVICES
Victim website: | gcbhs.com |
Victim country: | USA |
Attacker name: | DragonForce |
Attacker class: | Cybercrime |
Attack technique: | Data breach |
Ransom demand: | N/A |
Exfiltrated data amount: | 72.4 GB |
Exfiltrated data type: | Personal data of clients, financial documents, etc. |
Leaked data: | / |
Ransom deadline: | 15th Dec 23 |
Cyber Risk Factor: | 4 |
Image: |
Stay safe!
Hackmanac Team!
Latest news
HACKS OF TODAY 23/04/2024
Today's HOT includes 12 ransomware victims by the notorious Medusa, Abyss, RansomHouse, Cactus, RansomHub, BianLian, Qilin and Qiulong gangs. The average Cyber Risk Factor is 4.5. Read below...
Read MoreHACKS OF TODAY 20-21-22/04/2024
Today's HOT includes 10 ransomware victims by the notorious 8Base, Medusa, Embargo and Inc Ransom gangs. The average Cyber Risk Factor is 3.9. Read below the full list.
Read MoreHACKS OF TODAY 13-14-15/04/2024
Today's HOT includes 24 ransomware victims by the notorious Hunters International, LockBit 3.0, Daixin, Medusa, ThreeAM, Black Suit, DragonForce, 8Base, Akira and DarkVault gangs. The average Cyber...
Read More