news
HACKS OF TODAY 26/04/2024

Today’s HOT includes 19 victims by the notorious Rhysida, Everest, RansomHouse, DarkVault, RansomHub, Medusa, Hunters International, Cactus and dAn0n gangs.
The average Cyber Risk Factor is 4.2.
Read below the full list.
Disclaimer:
Data are collected from public info published on Dark Web.
The Cyber Risk factor is calculated on cyber attacks’ impact based on available data.
It shows the severity of an event: 1 = low, 5 = critical
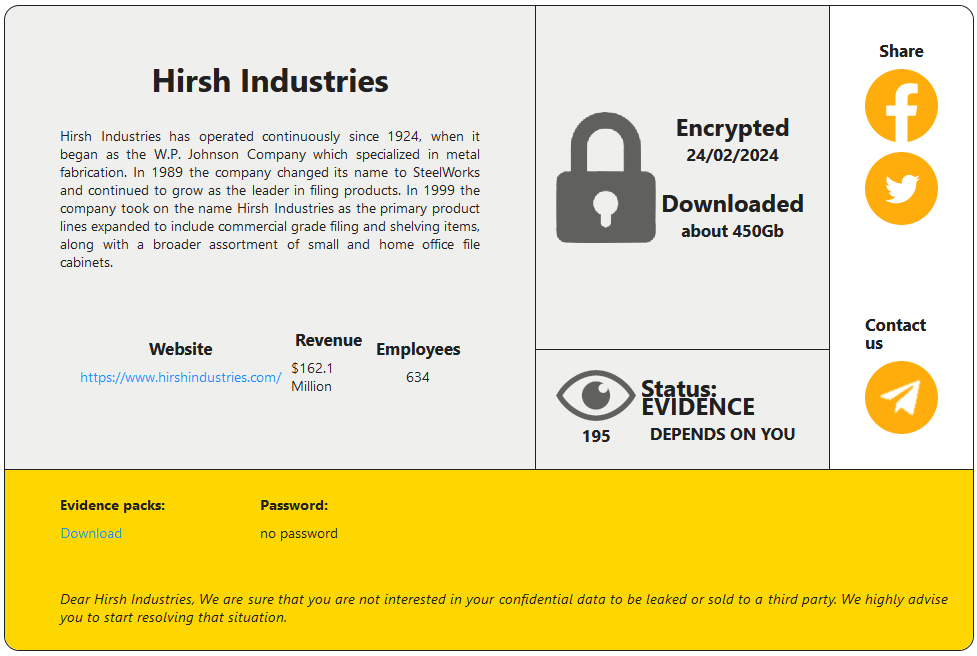
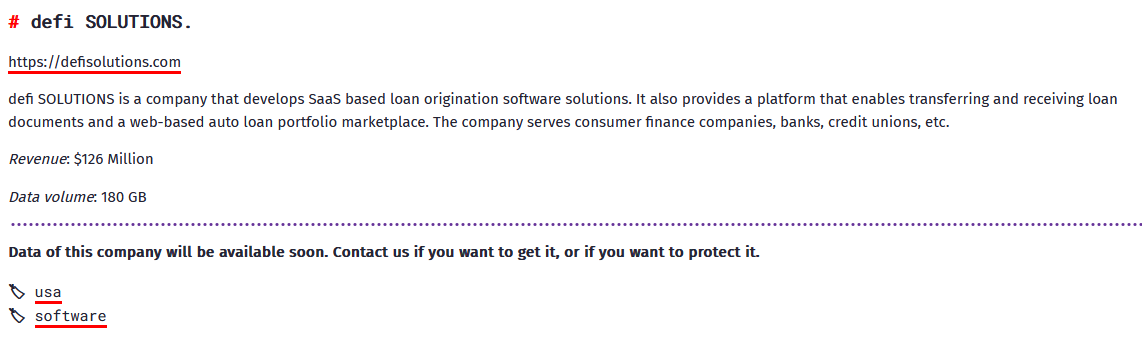
CDSHotels
LES MIROIRS ST-ANTOINE
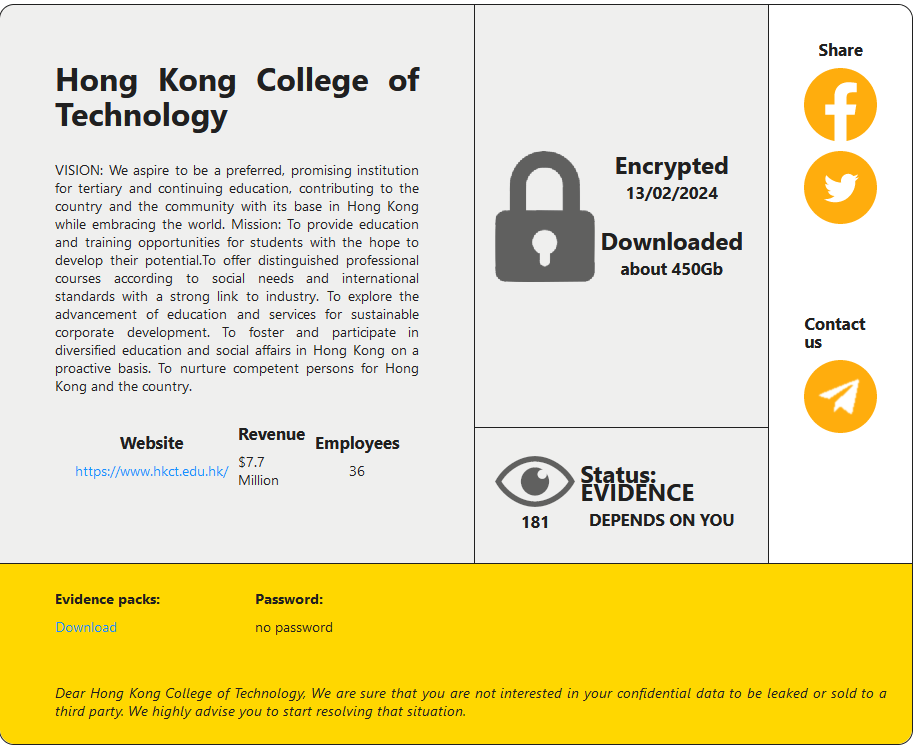
HONG KONG COLLEGE OF TECHNOLOGY
Victim website: | hkct.edu.hk |
Victim country: | Hong Kong |
Attacker name: | RansomHouse |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 450 GB |
Exfiltrated data type: | N/A |
Leaked data: | Sample |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
|
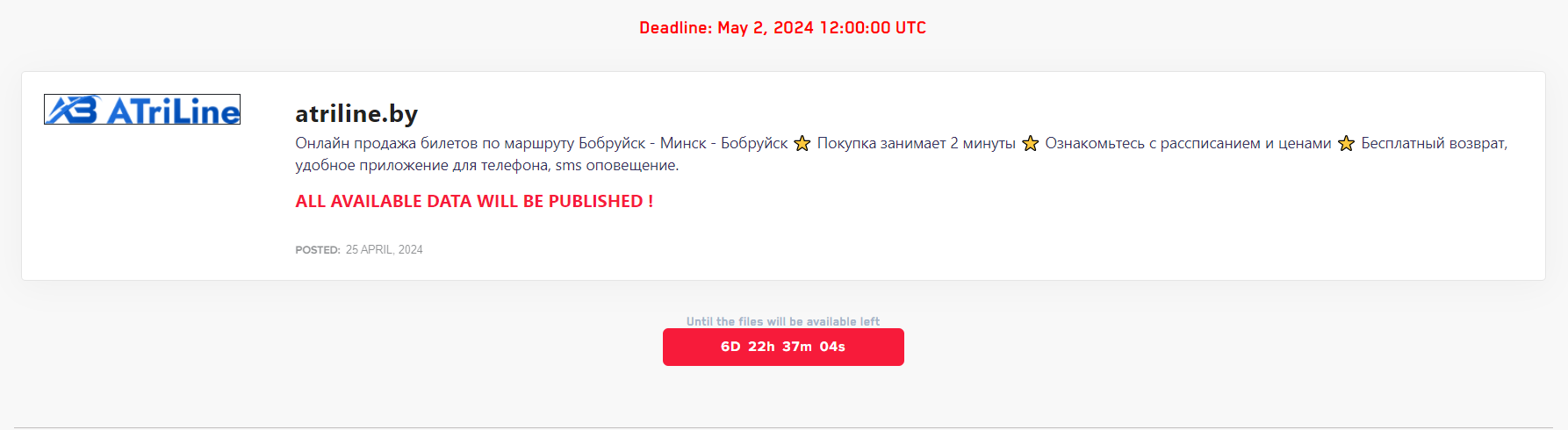
ATRILINE
Victim website: | atriline.by |
Victim country: | Belarus |
Attacker name: | DarkVault |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
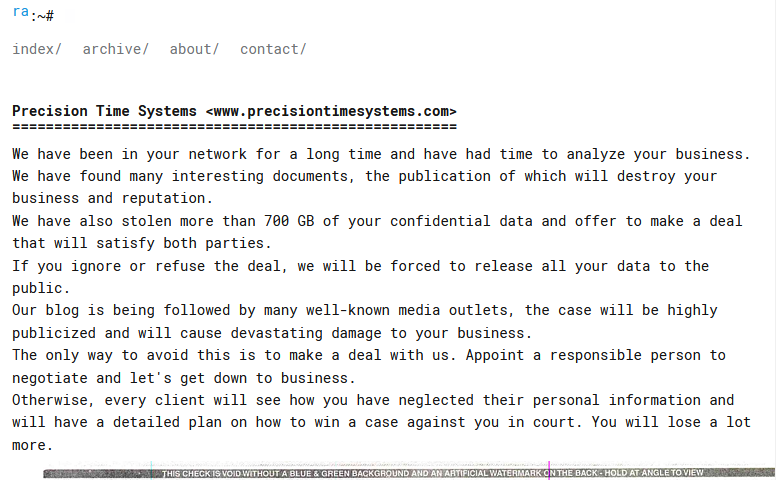
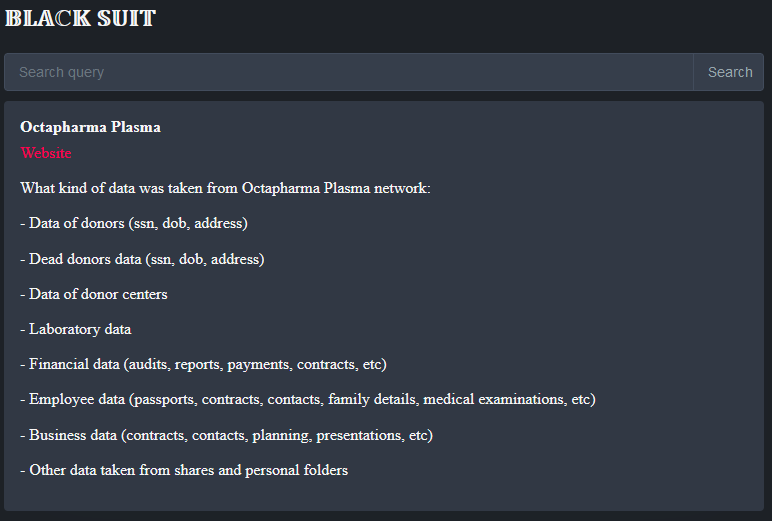
PRECISION TIME SYSTEMS
Victim website: | precisiontimesystems.com |
Victim country: | USA |
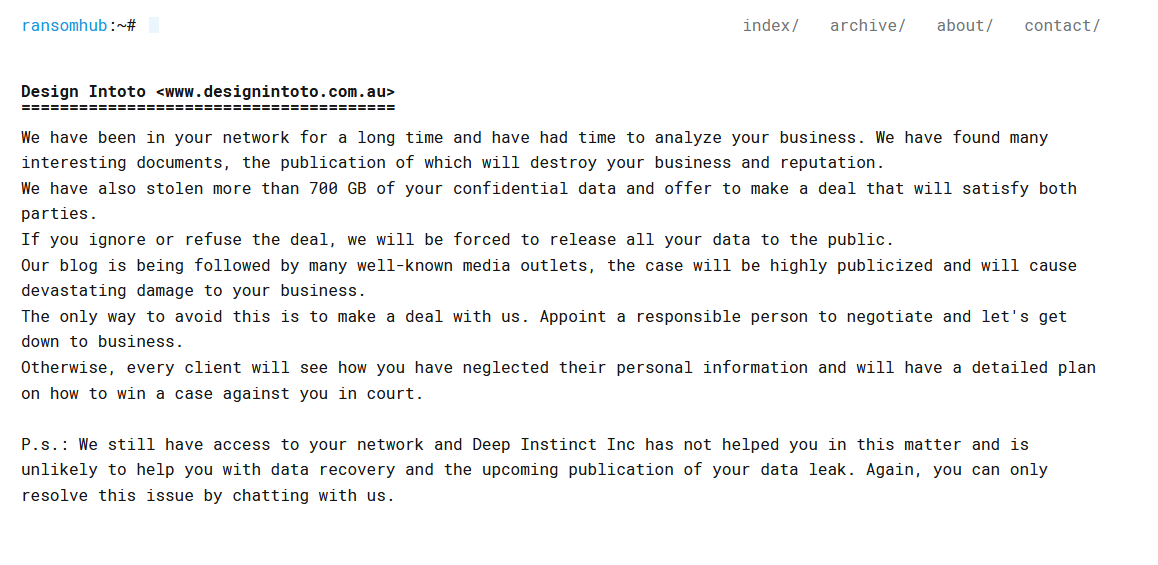
Attacker name: | RansomHub |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 700 GB |
Exfiltrated data type: | Financial data, insurance documents, contracts, etc. |
Leaked data: | Sample |
Ransom deadline: | 02nd May 24 |
Cyber Risk Factor: | 5 |
Image: |
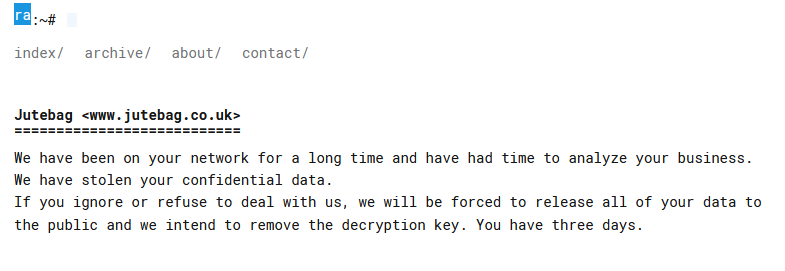
JUTEBAG
Victim website: | jutebag.co.uk |
Victim country: | United Kingdom |
Attacker name: | RansomHub |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 20 GB |
Exfiltrated data type: | Confidential data |
Leaked data: | / |
Ransom deadline: | 30th Apr 24 |
Cyber Risk Factor: | 4 |
Image: |
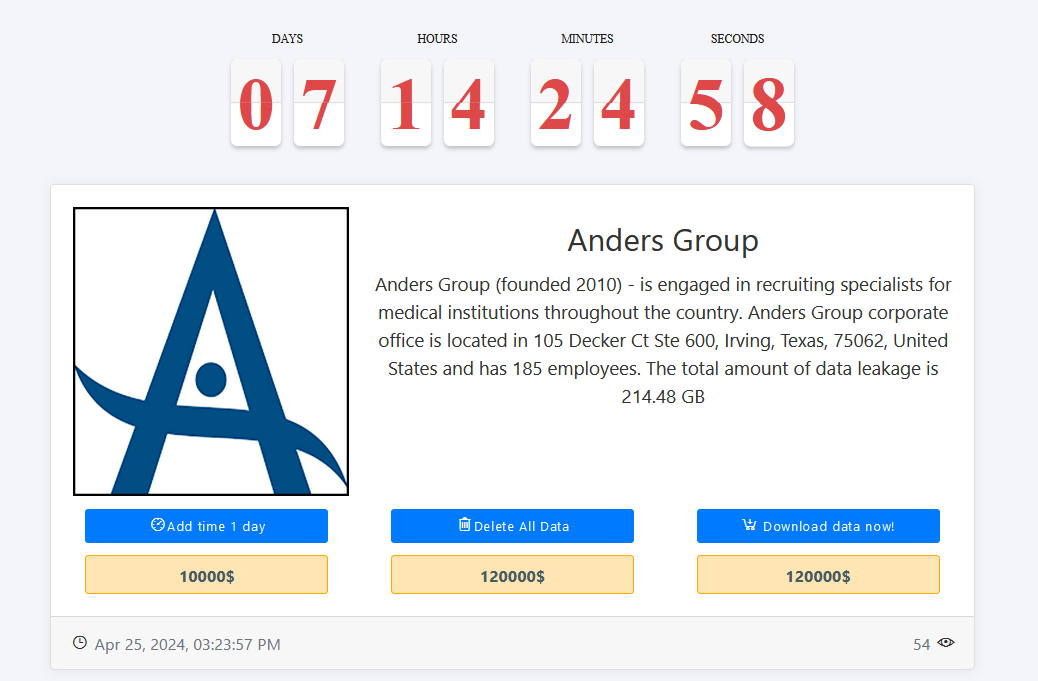
ANDERS GROUP
Victim website: | andersgroup.org |
Victim country: | USA |
Attacker name: | Medusa |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | $ 120,000 |
Exfiltrated data amount: | 214.48 GB |
Exfiltrated data type: | N/A |
Leaked data: | Sample |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
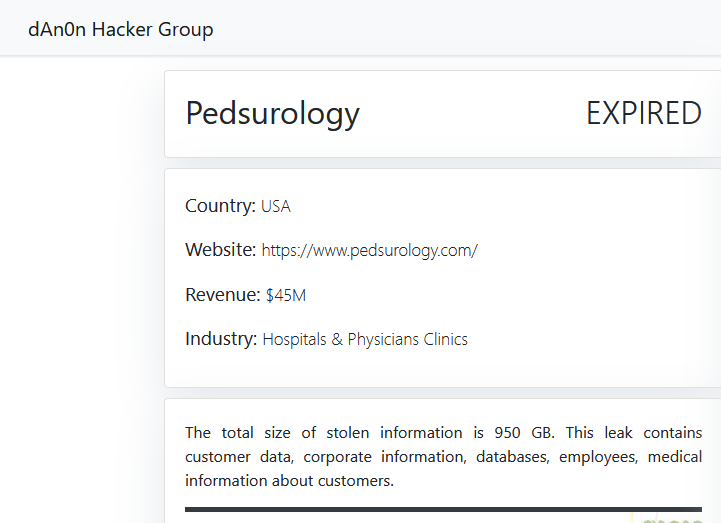
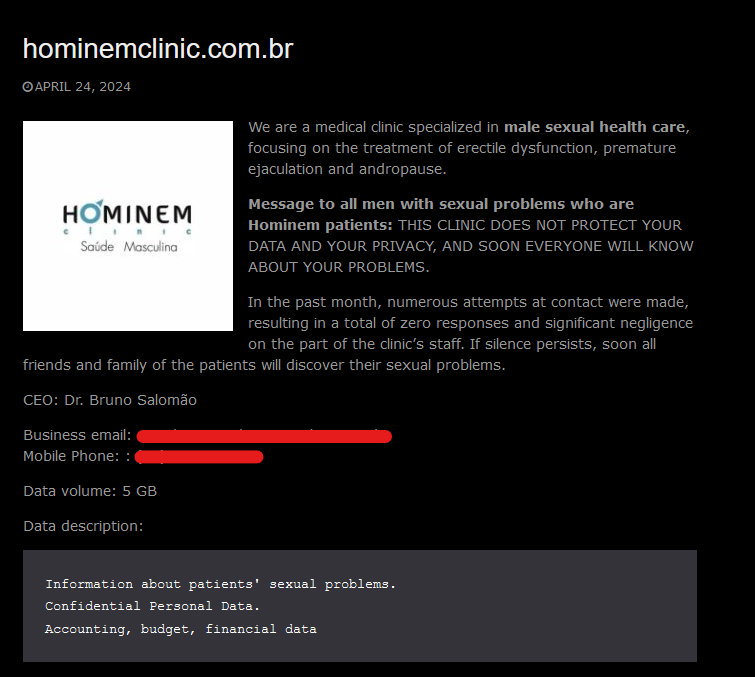
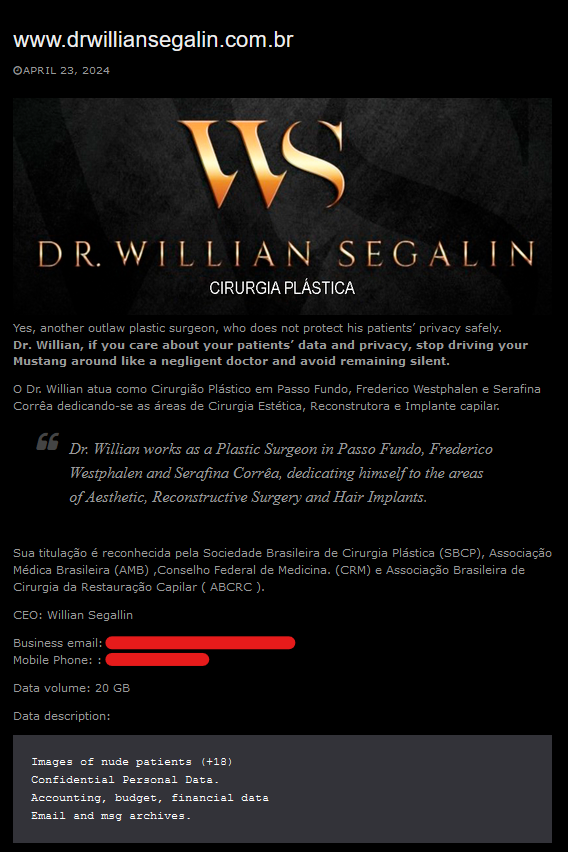
PEDIATRIC UROLOGY ASSOCIATES
Victim website: | pedsurology.com |
Victim country: | USA |
Attacker name: | dAn0n |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 950 GB |
Exfiltrated data type: | Customer data, corporate information, databases, employees, medical information about customers. |
Leaked data: | Sample |
Ransom deadline: | Expired |
Cyber Risk Factor: | 5 |
Image: |
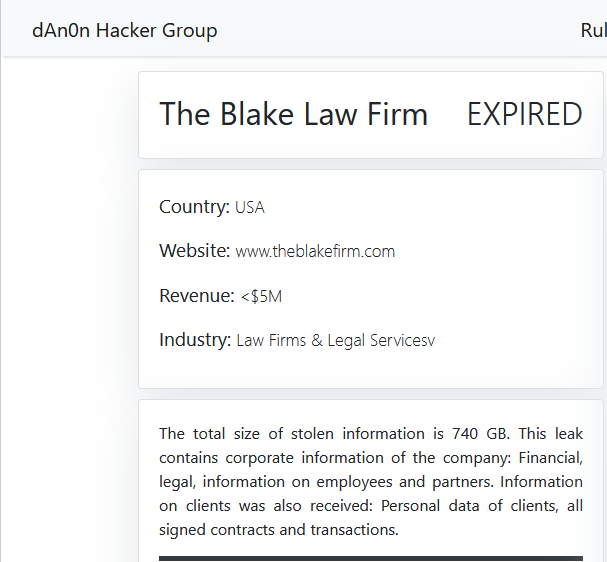
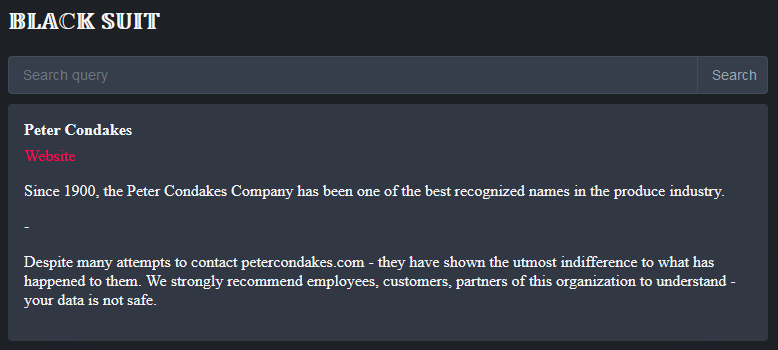
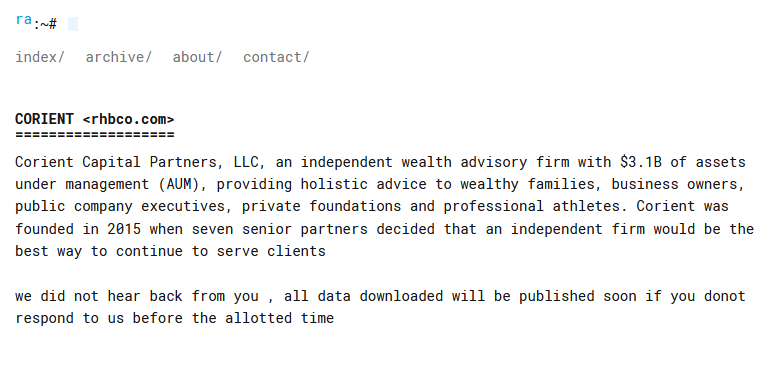
THE BLAKE LAW FIRM
Victim website: | theblakefirm.com |
Victim country: | USA |
Attacker name: | dAn0n |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 740 GB |
Exfiltrated data type: | Financial, legal, information on employees and partners. Information on clients was also received: Personal data of clients, all signed contracts and transactions. |
Leaked data: | Sample |
Ransom deadline: | Expired |
Cyber Risk Factor: | 5 |
Image: |
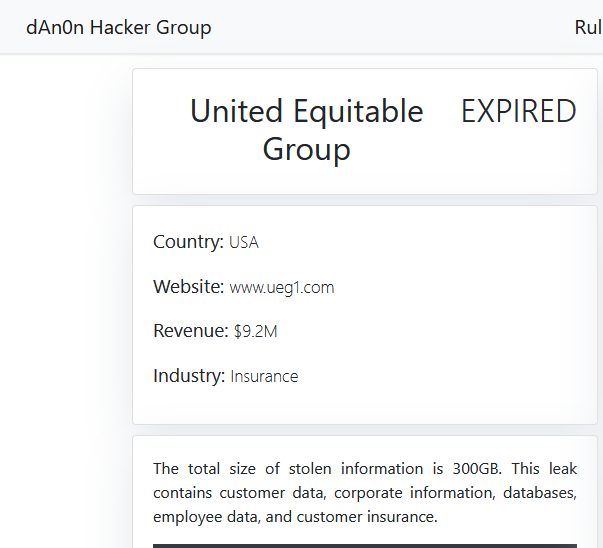
UNITED EQUITABLE GROUP
Victim website: | ueg1.com |
Victim country: | USA |
Attacker name: | dAn0n |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 300 GB |
Exfiltrated data type: | Customer data, corporate information, databases, employee data, and customer insurance. |
Leaked data: | Sample |
Ransom deadline: | Expired |
Cyber Risk Factor: | 4 |
Image: |
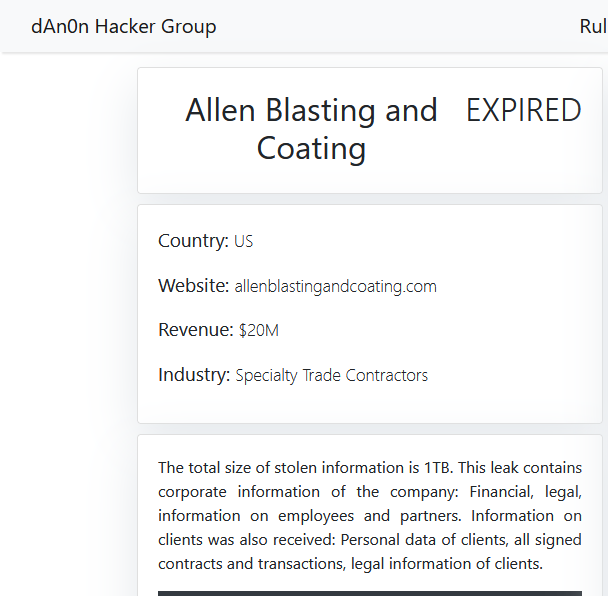
ALLEN BLASTING AND COATING
Victim website: | allenblastingandcoating.com |
Victim country: | USA |
Attacker name: | dAn0n |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 1 TB |
Exfiltrated data type: | Financial, legal, information on employees and partners. Information on clients was also received: Personal data of clients, all signed contracts and transactions, legal information of clients. |
Leaked data: | Sample |
Ransom deadline: | Expired |
Cyber Risk Factor: | 5 |
Image: |
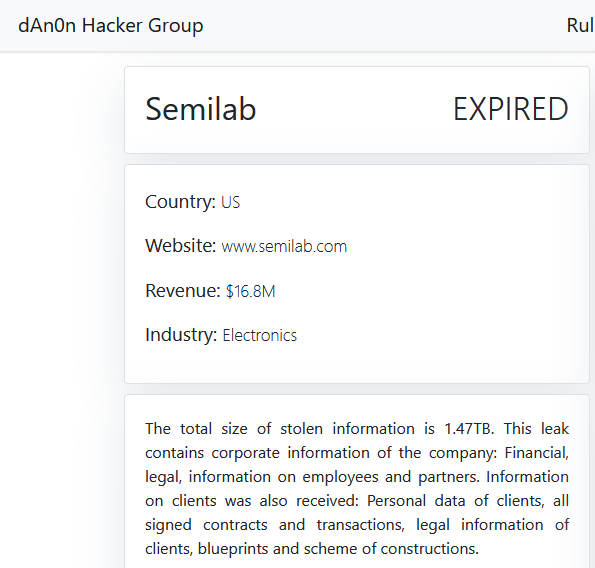
SEMILAB
Victim website: | semilab.com |
Victim country: | Hungary |
Attacker name: | dAn0n |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 1.47 TB |
Exfiltrated data type: | Financial, legal, information on employees and partners. Information on clients was also received: Personal data of clients, all signed contracts and transactions, legal information of clients, blueprints and scheme of constructions. |
Leaked data: | / |
Ransom deadline: | Expired |
Cyber Risk Factor: | 5 |
Image: |
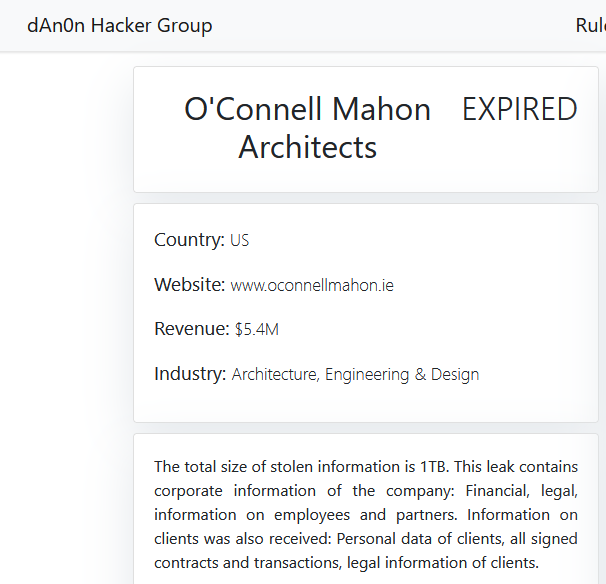
O’CONNELL MAHON ARCHITECTS
Victim website: | oconnellmahon.ie |
Victim country: | Ireland |
Attacker name: | dAn0n |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 1 TB |
Exfiltrated data type: | Financial, legal, information on employees and partners. Information on clients was also received: Personal data of clients, all signed contracts and transactions, legal information of clients. |
Leaked data: | / |
Ransom deadline: | Expired |
Cyber Risk Factor: | 5 |
Image: |
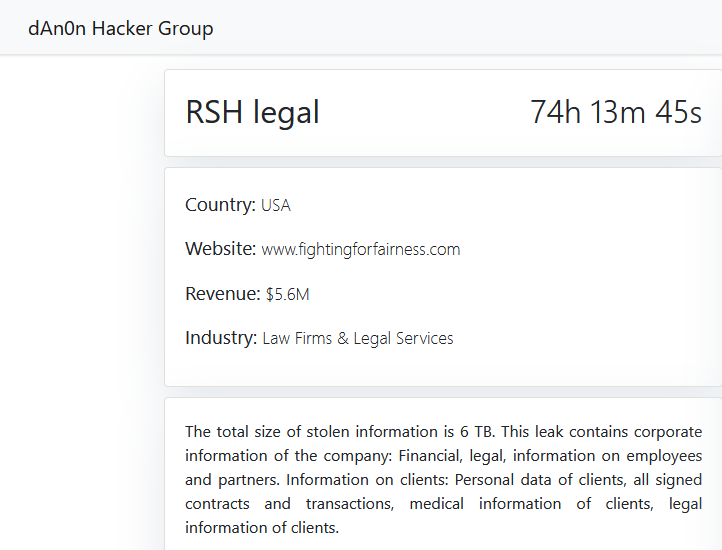
RSH LEGAL
Victim website: | fightingforfairness.com |
Victim country: | USA |
Attacker name: | dAn0n |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 6 TB |
Exfiltrated data type: | Financial, legal, information on employees and partners. Information on clients: Personal data of clients, all signed contracts and transactions, medical information of clients, legal information of clients. |
Leaked data: | / |
Ransom deadline: | 29th Apr 24 |
Cyber Risk Factor: | 5 |
Image: |
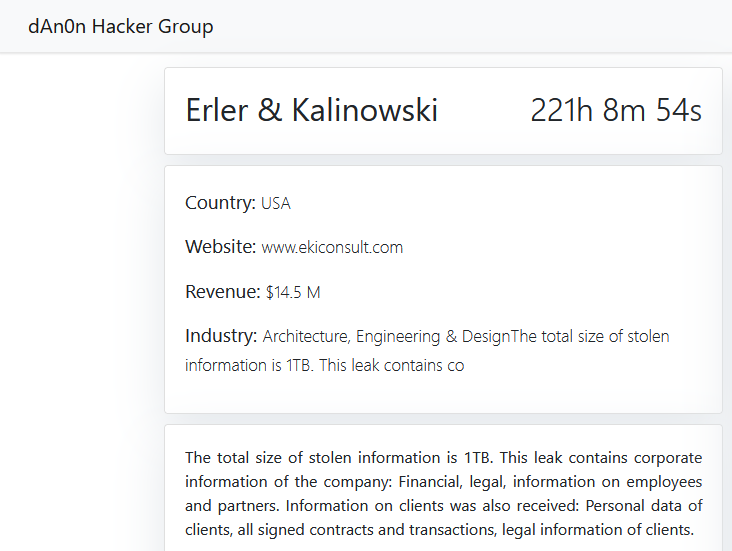
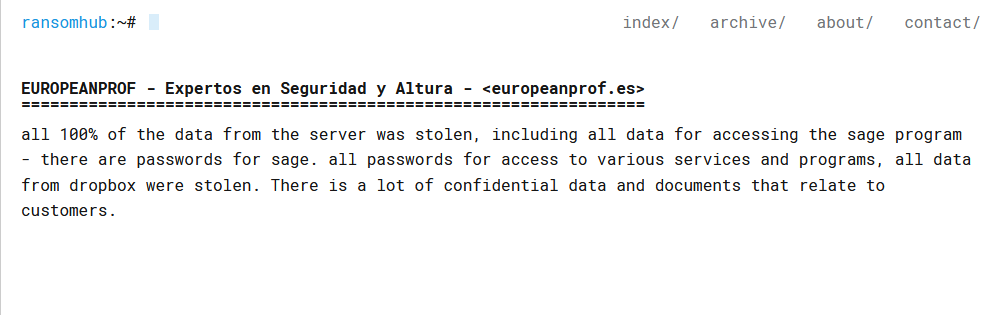
ERLER & KALINOWSKI
Victim website: | ekiconsult.com |
Victim country: | USA |
Attacker name: | dAn0n |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 1 TB |
Exfiltrated data type: | Financial, legal, information on employees and partners. Information on clients was also received: Personal data of clients, all signed contracts and transactions, legal information of clients. |
Leaked data: | / |
Ransom deadline: | 05th May 24 |
Cyber Risk Factor: | 5 |
Image: |
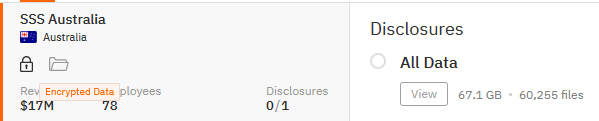
SSS AUSTRALIA
Victim website: | sssaustralia.com.au |
Victim country: | Australia |
Attacker name: | Hunters International |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 67.1 GB (60,255 files) |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
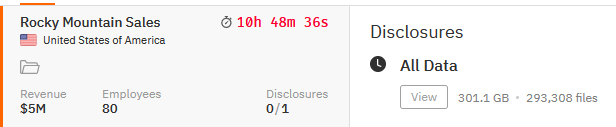
ROCKY MOUNTAIN SALES
Victim website: | rockymountainsales.com |
Victim country: | USA |
Attacker name: | Hunters International |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 301.1 GB (293,308 file) |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | 27th Apr 24 |
Cyber Risk Factor: | 4 |
Image: |
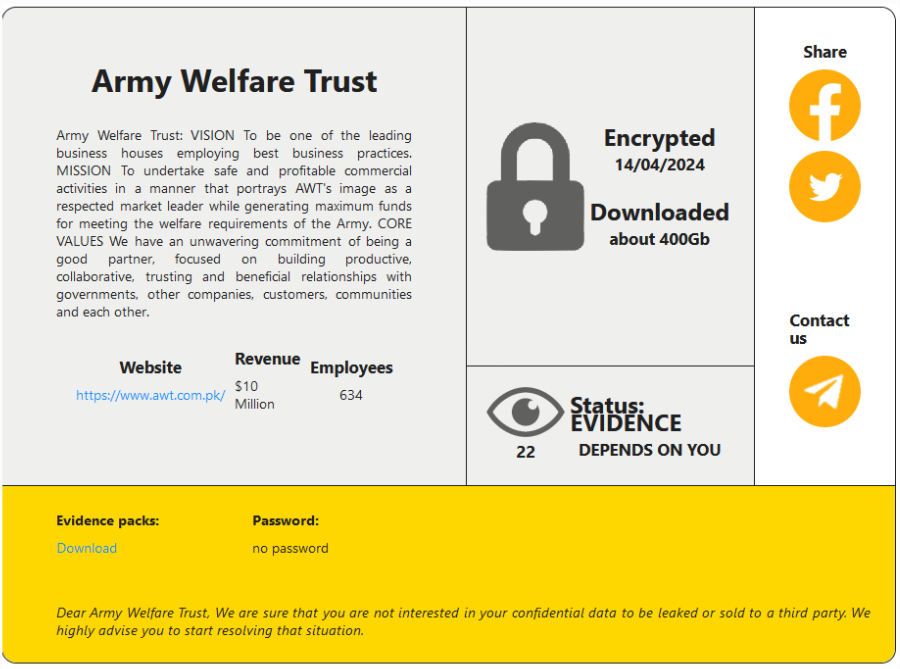
IDDINK GROUP
Victim website: | iddink.nl |
Victim country: | Netherlands |
Attacker name: | Cactus |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 460 GB |
Exfiltrated data type: | Personal identifying information, financial documents, customer data, database exports, various confidential documents, corporate correspondence, employees personal documents, private software sources, etc. |
Leaked data: | Sample |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
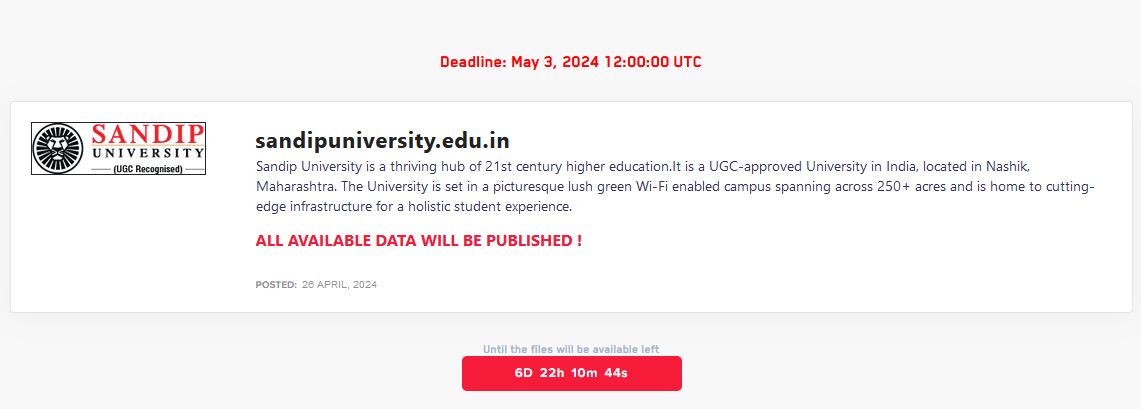
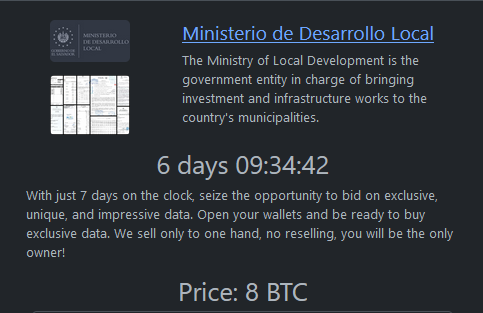
SANDIP UNIVERSITY
Victim website: | sandipuniversity.edu.in |
Victim country: | India |
Attacker name: | Dark Vault |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | 03rd May 24 |
Cyber Risk Factor: | 3 |
Image: |
Stay safe!
Hackmanac Team!
Latest news
HACKS OF TODAY 26/04/2024
Today's HOT includes 19 victims by the notorious Rhysida, Everest, RansomHouse, DarkVault, RansomHub, Medusa, Hunters International, Cactus and dAn0n gangs. The average Cyber Risk Factor is 4.2. Read...
Read MoreHACKS OF TODAY 25/04/2024
Today's HOT includes 8 ransomware victims by the notorious RansomHub, Hunters International, Black Suit, Qiulong, DarkVault, RansomHouse, Qilin and MyData gangs. The average Cyber Risk Factor is 4.0....
Read MoreHACKS OF TODAY 24/04/2024
Today's HOT includes 10 ransomware victims by the notorious RansomHouse, Black Suit, Rhysida, BianLian, RansomHub, BlackBasta, Eraleig and Qiulong gangs. The average Cyber Risk Factor is 4.4. Read...
Read More