news
LOCKBIT AND OPERATION CRONOS: THE DISRUPTION OF THE WORLD'S BIGGEST RANSOMWARE OPERATION

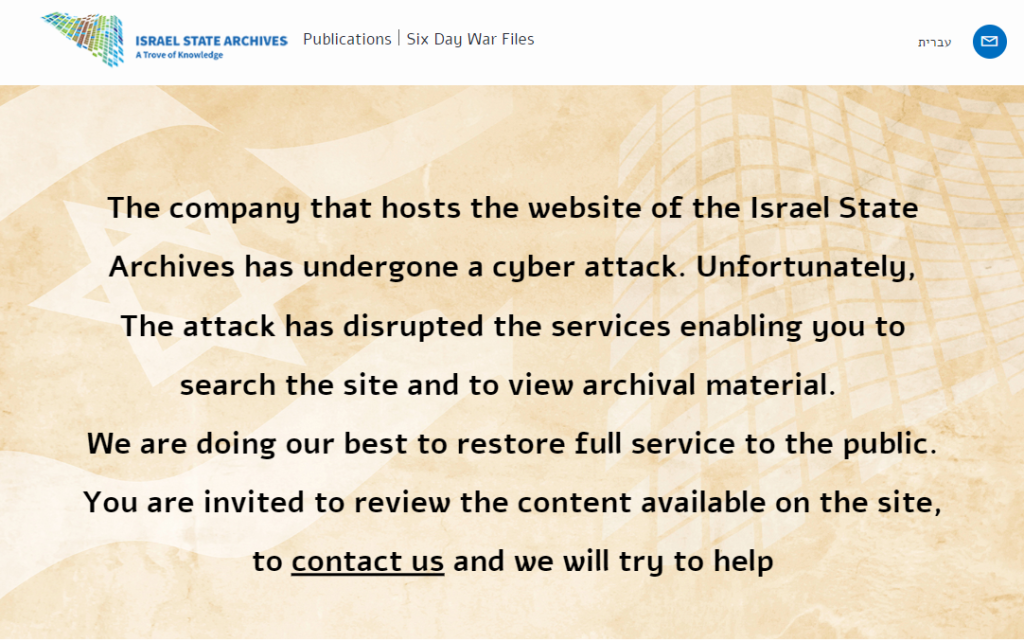
The NCA (National Crime Agency) today, Tuesday 20 February 2024, released public details about the international disruption campaign targeting LockBit, the world’s most harmful cyber crime group.
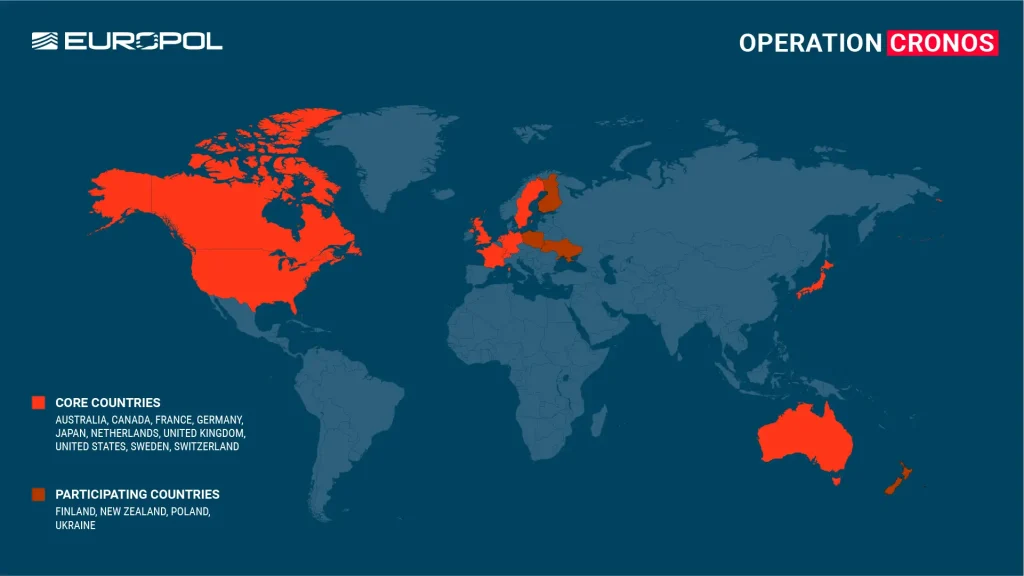
Led by the NCA with collaboration from the FBI, Europol and support from international partners across ten countries, the operation named Cronos involved covert infiltration of LockBit’s network, resulting in control over their services and compromising their criminal enterprise.
The world’s most harmful ransomware operation
First emerged at the end of 2019, with the name of “ABCD ransomware“, LockBit grown rapidly and soon became the most deployed ransomware variant.
The success of LockBit were assured by the ransomware-as-a-service schema they provided, allowing affiliates to execute attacks using the group tools and infrastructure.
The group is also famous for experimenting new method such as the “Triple extortion” which incorporates DDoS (Distributed Denial of Service) attacks as an additional layer of pressure.
LockBit attacks led to billions in losses due to ransom payments and recovery costs.
Operation Cronos Achievements
The operation resulted in the capture of LockBit’s crucial administrative and public data leak platforms, significantly hindering their operational capabilities.
This led to the recovery of the LockBit platform’s source code and valuable intelligence on the group’s operations and collaborators.
Authorities confiscated the organization’s infrastructure and took down 34 servers in the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States and the United Kingdom. Additionally, two LockBit actors were arrested in Poland and Ukraine.
Over 200 cryptocurrency accounts associated with LockBit were frozen, and several individuals were charged criminally in the United States for their involvement in LockBit’s cyberattacks.
The operation inflicted considerable damage on LockBit’s operational abilities and reputation, disrupting their ransomware dissemination and data leaking activities.
Authorities recovered more than 1,000 decryption keys, aiding victims in restoring their encrypted data.
Efforts persist in dismantling LockBit’s network and pursuing individuals linked to the group.
Furthermore, decryption tools were developed to help victims, now accessible via the ‘No More Ransom‘ website.
The NCA, FBI, and the United States Department of Justice hailed the operation as a landmark success in countering cybercrime, managing to infiltrate and dismantle the cybercriminal syndicate.
This operation underscores the complex and organized nature of the cybercriminals behind LockBit and showcases the global commitment to thwarting their schemes.

Operation Cronos marks a critical turning point in the battle against cybercrime, underscoring the power of global collaboration and cutting-edge investigative methods in breaking down complex cybercriminal enterprises.
Businesses and institutions are urged to report any ransomware attacks, aiding law enforcement efforts and minimizing harm.
Additionally, the sophisticated nature of these cybercriminal groups serves as a clear reminder of the necessity for strong cybersecurity defenses to avert such incidents.
Latest news
HACKS OF TODAY 26/04/2024
Today's HOT includes 19 victims by the notorious Rhysida, Everest, RansomHouse, DarkVault, RansomHub, Medusa, Hunters International, Cactus and dAn0n gangs. The average Cyber Risk Factor is 4.2. Read...
Read MoreHACKS OF TODAY 25/04/2024
Today's HOT includes 8 ransomware victims by the notorious RansomHub, Hunters International, Black Suit, Qiulong, DarkVault, RansomHouse, Qilin and MyData gangs. The average Cyber Risk Factor is 4.0....
Read MoreHACKS OF TODAY 24/04/2024
Today's HOT includes 10 ransomware victims by the notorious RansomHouse, Black Suit, Rhysida, BianLian, RansomHub, BlackBasta, Eraleig and Qiulong gangs. The average Cyber Risk Factor is 4.4. Read...
Read More