news
HACKS OF TODAY 07/12/2023

Today’s HOT includes 18 ransomware victims by the notorious ALPHV/BlackCat, LockBit 3.0, Medusa, 8Base, Akira, INC Ransom, Monti, Cactus, Metaencryptor and Qilin gangs.
The average Cyber Risk Factor is 4.1.
Read below the full list.
Disclaimer:
Data are collected from public info published on Dark Web.
The Cyber Risk factor is calculated on cyber attacks’ impact based on available data.
It shows the severity of an event: 1 = low, 5 = critical
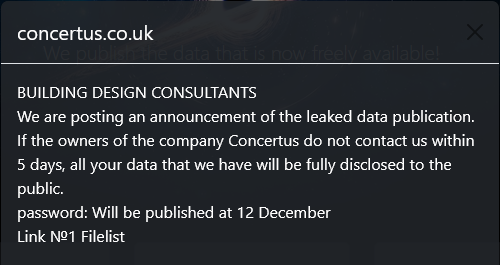
CAMPBELL COUNTY SCHOOLS
Victim website: | ccsd.k12.wy.us |
Victim country: | USA |
Attacker name: | Medusa |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | $ 600,000 |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | Miscellaneous documents |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | 21st Dec 23 |
Cyber Risk Factor: | 5 |
Image: |
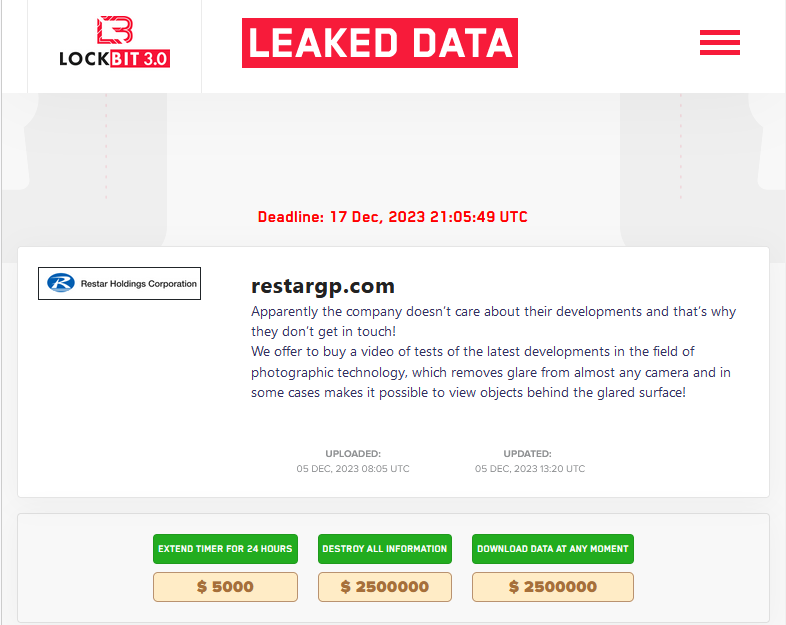
DIRECT RADIOLOGY
Victim website: | directradiology.com |
Victim country: | USA |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | Patient records, doctor docs, and company data |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | 14th Dec 23 |
Cyber Risk Factor: | 5 |
Image: |
CITIZENS BANK OF WEST VIRGINIA
Victim website: | citizenswv.com |
Victim country: | USA |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | $ 799,999 |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | Miscellaneous documents including financial data, etc. |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | 09th Dec 23 |
Cyber Risk Factor: | 5 |
Image: |
NEUROLOGY CENTER OF NEVADA
Victim website: | neurocnv.com |
Victim country: | USA |
Attacker name: | Qilin |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 198.2 GB |
Exfiltrated data type: | Confidential documents, invoices, scans, etc. |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 5 |
Image: |
TRI-CITY MEDICAL CENTER
Victim website: | tricitymed.org |
Victim country: | USA |
Attacker name: | INC Ransom |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | Forms, employees’ data, financial documents, invoices, etc. |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 5 |
Image: |
GERMAN ENERGY AGENCY
Victim website: | dena.de |
Victim country: | Germany |
Attacker name: | ALPHV/BlackCat |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | Sensitive data, mail correspondence, etc. |
Leaked data: | / |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
TRYAX REALTY MANAGEMENT
Victim website: | tryaxrealtymanagement.com |
Victim country: | USA |
Attacker name: | Monti |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 50 GB |
Exfiltrated data type: | NYS ERAP, personal data of employees, their lawsuits, passports, driver’s licenses, etc. |
Leaked data: | / |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
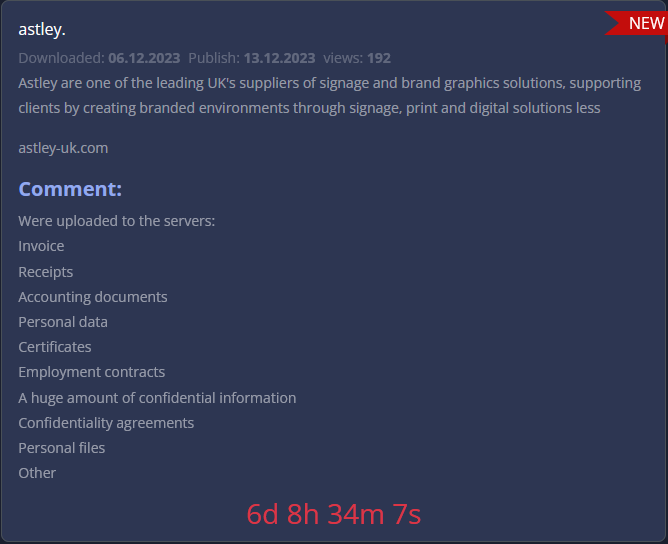
VISAN
Victim website: | visan.es |
Victim country: | Spain |
Attacker name: | 8Base |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | invoices, receipts, accounting documents, personal data, employment contracts, confidentiality agreements, and personal files. |
Leaked data: | / |
Ransom deadline: | 14th Dec 23 |
Cyber Risk Factor: | 3 |
Image: |
UNIVERSITÉ DE SHERBROOKE
Victim website: | usherbrooke.ca |
Victim country: | Canada |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | Miscellaneous documents including non-disclosure agreements, invoices, etc. |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | 14th Dec 23 |
Cyber Risk Factor: | 4 |
Image: |
HOPTO
Victim website: | hopto.com |
Victim country: | UAS |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | 14th Dec 23 |
Cyber Risk Factor: | 3 |
Image: |
BRIDGERS & PAXTON
Victim website: | bpce.com |
Victim country: | USA |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | 14th Dec 23 |
Cyber Risk Factor: | 3 |
Image: |
SIGNIFLOW
Victim website: | signiflow.com |
Victim country: | United Kingdom |
Attacker name: | LockBit 3.0 |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | Clients, contracts, NDAs, project information, client network credentials, etc. |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | 14th Dec 23 |
Cyber Risk Factor: | 4 |
Image: |
NATIONAL NAIL CORP
Victim website: | nationalnail.com |
Victim country: | USA |
Attacker name: | Cactus |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | Non-disclosure documents, ID cards, employees’ data, etc. |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
CIE AUTOMOTIVE
Victim website: | cieautomotive.com |
Victim country: | Spain |
Attacker name: | Cactus |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | N/A |
Exfiltrated data type: | ID cards, confidential documents, purchase orders, etc. |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
WARE PET PRODUCTS
Victim website: | warepet.com |
Victim country: | USA |
Attacker name: | Qilin |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 194.4 GB |
Exfiltrated data type: | Financial documents, employees’ data, etc. |
Leaked data: | Sample with proof of the exfiltrated data |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
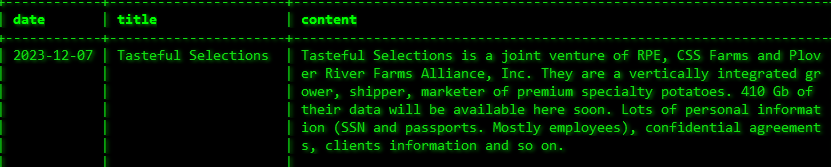
TASTEFUL SELECTIONS
Victim website: | tastefulselections.com |
Victim country: | USA |
Attacker name: | Akira |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 410 GB |
Exfiltrated data type: | Social Security numbers, passports, confidential agreements, client information, and more. |
Leaked data: | / |
Ransom deadline: | N/A |
Cyber Risk Factor: | 4 |
Image: |
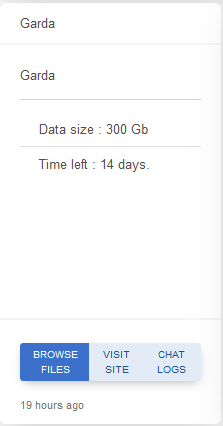
GARDAWORLD
Victim website: | garda.com |
Victim country: | Canada |
Attacker name: | Metaencryptor |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 300 GB |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | 22nd Dec 23 |
Cyber Risk Factor: | 4 |
Image: |
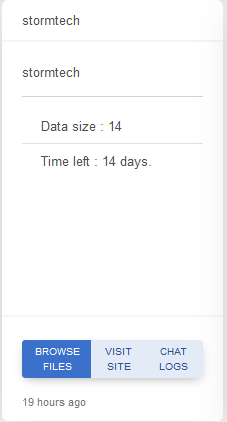
STORMTECH
Victim website: | stormtech.com |
Victim country: | USA |
Attacker name: | Metaencryptor |
Attacker class: | Cybercrime |
Attack technique: | Ransomware |
Ransom demand: | N/A |
Exfiltrated data amount: | 14 GB |
Exfiltrated data type: | N/A |
Leaked data: | / |
Ransom deadline: | 22nd Dec 23 |
Cyber Risk Factor: | 3 |
Image: |
Stay safe!
Hackmanac Team!
Latest news
HACKS OF TODAY 26/04/2024
Today's HOT includes 19 victims by the notorious Rhysida, Everest, RansomHouse, DarkVault, RansomHub, Medusa, Hunters International, Cactus and dAn0n gangs. The average Cyber Risk Factor is 4.2. Read...
Read MoreHACKS OF TODAY 25/04/2024
Today's HOT includes 8 ransomware victims by the notorious RansomHub, Hunters International, Black Suit, Qiulong, DarkVault, RansomHouse, Qilin and MyData gangs. The average Cyber Risk Factor is 4.0....
Read MoreHACKS OF TODAY 24/04/2024
Today's HOT includes 10 ransomware victims by the notorious RansomHouse, Black Suit, Rhysida, BianLian, RansomHub, BlackBasta, Eraleig and Qiulong gangs. The average Cyber Risk Factor is 4.4. Read...
Read More